Want to see Parasoft in action? Sign up for our Monthly Demos! See Demos & Events >>
Want to see Parasoft in action? Sign up for our Monthly Demos! See Demos & Events >>
 Reading Time: 9 minutes
Reading Time: 9 minutesMISRA is the legendary standard against which development teams measure a large portion of today’s software. But exactly what is MISRA, how did it develop, how do C and C++ developers gage standards against it, and how do they know they are in compliance?
In this piece, we examine the compelling background of how MISRA came to be. We also answer the above questions and reveal how MISRA helps C++ and C code programmers write efficiently while addressing current safety and security concerns.
Specifically, we look at:
The MISRA standards contain guidelines and code rules for writing software. The automotive, aerospace and defense, medical, industrial automation, and railway industries, among others, use the standard to help their developers write source code that ensures safety, security, and reliability in the software. Because embedded software engineers use the C and C++ programming languages to write code for safety-critical software, the creators of the MISRA standard built them for coders who use these two languages.
The Motor Industry Software Reliability Association (MISRA) consortium is similar to the ISO (International Standards Organization) and the IEC (International Electrotechnical Commission), which set general compliance guidelines for industry, such as standards for the development of electric/electronic systems. ISO 26262, published in 2011, is the international standard for certifying the safety of electronics on road vehicles. Software systems that have achieved ISO/IEC compliance can be certified by verification authorities as safe.
MISRA, a consortium of automotive-related industries, developed its first guidelines in 1998, MISRA c1998. The consortium came together as a result of the UK Safety Critical Systems Research Programme, which the UK government instituted to address some of the challenges that the automobile industry faced due to the increased use of software in the manufacture and operation of vehicles. Some of the original industries that helped develop the standard, all of whom are also currently active steering-committee members, included:
Although the consortium originally created the standard for the automotive industry, other embedded industries have adopted the standard, including those that use embedded technology that connects devices like loT systems.
In the early 1990s, electronics were becoming more and more important in automobiles. So too was the embedded software that was an integral part of these electronics. Thus, engineers and manufacturers began to realize that the reliability of the software was vitally important, for both safety and commercial reasons. The challenge is even greater today because software for a single car can involve in excess of 100 million lines of coding.
Automotive manufacturers use software in engine and powertrain operations. It monitors and provides the correct amount of fuel in ICEs (internal combustion engines) and it supplies data to the ECM (engine control module, sometimes called an ECU, or engine control unit). This is the main automotive computer that gathers information about fuel consumption, the power the engine generates, emissions, and other vital engine-related data essential for safe and efficient driving. (Electric and hybrid vehicles have similar software requirements related to the engine and powertrain.)
Manufacturers also employ software to operate onboard computers for the ubiquitous sensors on current vehicles, including door and window monitoring, climate control systems, and parking and traffic sensors. They also use them in safety-critical systems like airbags and ABS. More operation-related software is certainly in the future of road vehicles, with engineers and designers devoting serious attention to self-driving capabilities, improved energy efficiency, and enhanced safety.
Industries throughout the world accept the MISRA C rules for writing safety- and security-critical C code. The rules and guidelines inspire confidence because they are readable, concise and because they focus on essentials. While applying the MISRA standard does not guarantee that software is free of security and quality problems, it helps software engineers write code that is safer, more robust, more portable, and easier to maintain. (MISRA guidelines also address security vulnerabilities but other coding standards like CERT C specifically tackle security issues written into code.)
Today, development teams employ coding standards as a method to define, manage, and utilize a group of coding practices, with the prime objective being consistency. The main aim of a coding rule is to limit use of the language so it prevents the developer from doing things that are “wrong” and can be potentially dangerous.
Developers can avoid many defects in software by adopting sensible language-use restrictions. This results in style uniformity, which is valuable as a discipline in a software project.
The versatility aspect of the C++ and C languages allows a developer to write code that can be unintentionally incorrect and possibly dangerous. It is easy for him or her to write code that adheres to the requirements of the language’s standard but this, nonetheless, can result in undesirable behavior and program “crashes.” These include, for example, code that accesses memory beyond the parameters of an arithmetic process, or of an array that results in memory or boundary violations.
It is obviously important to identify these potential problems. But the aim of MISRA is to prevent problems, not simply identify them. A compiler can detect some of them but using a dedicated analysis tool is more effective.
The MISRA standard emphasizes that adhering to coding rules is only one component to developing software successfully. Developers must integrate each programming project into a disciplined engineering setting that includes methodical development workflows and applying proven in-use validation tools.
Each MISRA standard embodies a set of coding parameters and rules, plus support materials. The support materials are a supplemental part of the standard and provide important background information essential for any programmer who wants to obtain compliance.
Let’s look at the current C and C++ MISRA coding standards themselves and at brief descriptions.
The MISRA coding standard furnishes thorough rules and guidelines so companies can protect their applications against run-time errors and software failures, and make them less prone to security and safety vulnerabilities. Compliance with the MISRA standard helps improve syntax, creates code conformity, and facilitates portability. For teams that don’t use static analysis (or SAST – Static Application Security Testing) solutions or tools, validating compliance can be problematic. Parasoft simplifies the process, which is critical for ensuring timely software delivery and coding security.
To achieve successful compliance, solutions need to offer:
It's important to apply MISRA compliance throughout the software development lifecycle, including during code implementation for shift left testing and to expedite code reviews. This provides not only quality improvements but progress metrics, ongoing traceability, and enforcement. Automating documentation and compliance reporting per MISRA Compliance 2020 is also a key factor for conserving resources and time, and for avoiding frustration when dealing with fixing the violations themselves.
Tools like Parasoft can be configured to detect a subset of the entire MISRA standards. This reduces the amount of noise produced from the analysis and increases focus on addressing severe violations.
One of the problems associated with companies achieving MISRA compliance has been the absence of a standard mechanism for demonstrating compliance. To address this issue, MISRA published “MISRA Compliance 2020: Achieving Compliance with MISRA Coding Guidelines,” which is the latest update that provides a more concrete definition of “MISRA compliance” and identifies several deliverables required for demonstrating compliance with the MISRA standard.
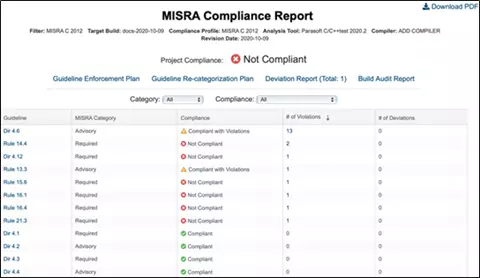
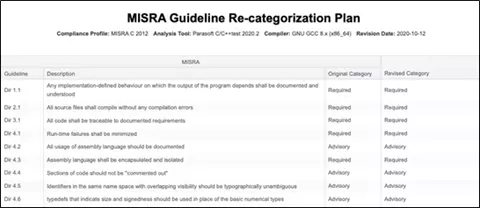
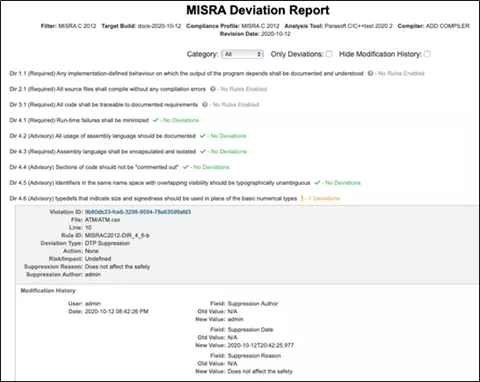
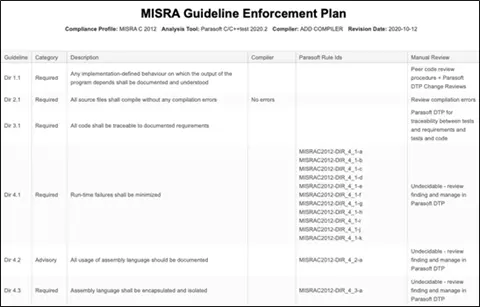
Certified by TÜV SÜD, C/C++test automates the application and monitoring of analysis coding criteria like MISRA. This includes a unit test platform. This platform integrates creating tests and executing them, and also coverage reporting. Then Parasoft’s centralized analytics and reporting hub Parasoft DTP, which is also TÜV certified, aggregates and correlates analysis and test data from the Parasoft C/C++test.
It’s a fact that developers re-use legacy code for safety-critical software. However, re-using legacy code and realizing complete MISRA C 2012 compliance can be daunting.
MISRA compliance is much easier to manage and achieve as code is being written. The MISRA C 2012 document even provides a warning that we can interpret when applying it to legacy programs:
“ … a project that checks for MISRA compliance late in its cycle is likely to spend a considerable amount of time re-coding, re-reviewing, and re-testing. It’s therefore expected that the software development process will require the early application of MISRA C principles.”
Noting re-use of legacy software, the MISRA Consortium Limited, the organization responsible for creating and maintaining the MISRA standard, created today’s updated and current release of MISRA Compliance:2020. This document provides guidance for developers who write new code and for those who are using adopted or legacy code.
However, the distinction may not be totally clear. For example, during product development, a coder writes software for a prototype only to find out that the project needs MISRA compliance, so he or she must backtrack and apply the guidelines. While this is not applying MISRA to legacy code, it is similar in that when the code is scanned or analyzed, the results reveal thousands, if not tens of thousands, of violations. Add this to the fact that writers of embedded software often state that developing fully compliant code is too difficult, the task to comply with MISRA may appear overwhelming. But it is possible to find a realistic middle ground between “daunting” and compliance.
MISRA Compliance 2020 helps clarify how to prove and demonstrate conformance at a project’s end. Delivering the four mandatory documents is a must. Consider the following for legacy and new code compliance:
Parasoft automates the necessary reports to assist businesses in satisfying the MISRA 2020 Compliance agenda.
It’s smart to establish a workflow to fix violations on a reasonable schedule without interrupting the development of code and therefore degrading it. Crucial recommendations include:
To make this easier, Parasoft’s DTP reporting hub includes a compliance status dashboard.
The goal of qualifying tools is to certify that they are valid for the use intended. It includes proof of how the team came to qualify them and the rationale behind it. Parasoft C/C++test and our reporting tool, Parasoft DTP have been TÜV SÜD certified for use on safety-critical applications, and a tool qualification kit exists for some of the strictest process standards like DO-178B/C and what they require.
The MISRA standard also stresses competency, expertise, and training of staff as key factors for evaluating product readiness. This includes recognizing the risks of violations, and properly configuring and using development tools and static analysis.
It's important to support MISRA compliance throughout the software development lifecycle. Reaching compliance with MISRA is easier with Parasoft's comprehensive solution. With ongoing enforcement, traceability, and automating documentation, teams can save time, resources, and alleviate frustrations that come with adhering to this guideline.
“MISRA”, “MISRA C” and the triangle logo are registered trademarks of The MISRA Consortium Limited. ©The MISRA Consortium Limited, 2021. All rights reserved.
A Sr. Technical Product Marketing Manager for Parasoft’s embedded testing solutions, Ricardo has expertise in the SDLC and test automation of embedded real time, safety, and security-critical applications, and software compliance to industry standards.